What are Nmap Scripts or NSE?
Have you heard about the Nmap? If not please read the article nmap commands in Kali Linux
If you don’t want to read the article, no problem at all, I am going to give a short description of Nmap.
Nmap is a powerful tool for scanning networks and finding out live systems, open ports, and running services. This tool is available for windows and Linux.
But if you want deeper information about the target machine you must use the Nmap scripting engine. I will describe step by step for beginners.
You will feel it as a knife on cack.
The Nmap Scripting Engine (NSE) is one of Nmap’s most influential and adaptable features. It permits clients to compose (and offer) straightforward scripts to automate a wide variety of systems networking tasks. Those Nmap scripts are then executed in parallel with the fast speed and productivity you anticipate from Nmap. Clients can depend on the developing and assorted set of scripts conveyed with Nmap, or compose their own particular to help. Here I am going to check
So what is now, Check out the Nmap script’s location. You can use the following command to see all Available scripts in nmap.
#locate *.nse
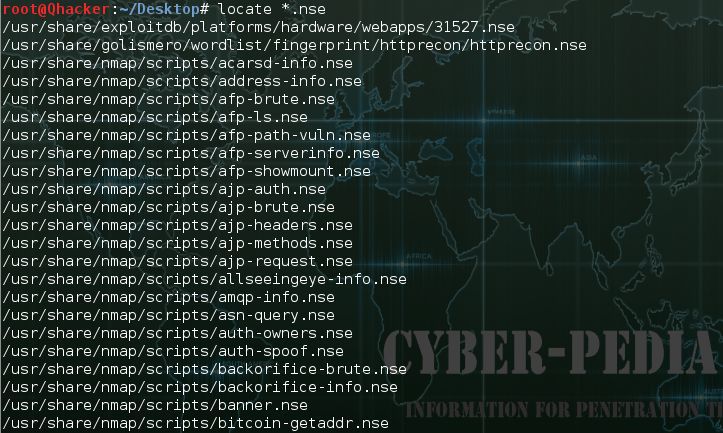
Nmap scripts Examples
–script-help
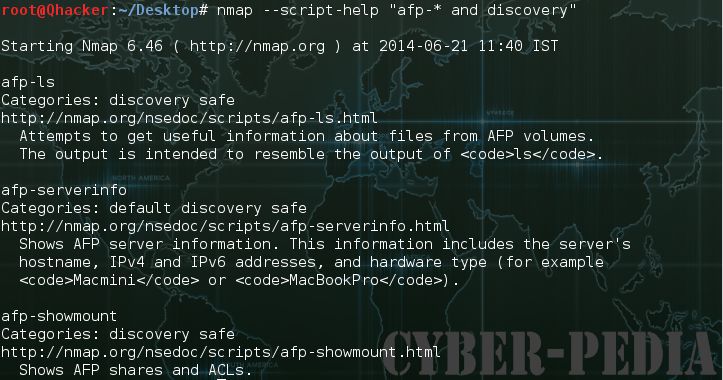
Shows help with Nmap scripts. For each script matching the given detail, Nmap prints the script name, its classifications, and its categories. The determinations are the same as those acknowledged by -script; so for instance on the off chance that you need help with the afp- and discovery, you would run the following command
#nmap –script-help “afp-* and discovery”.
–script-trace
This alternative works at the requisition level instead of the parcel by the bundle. In the event that this alternative is pointed out, all approaching and friendly correspondence performed by scripts is printed. The showed data incorporates the correspondence convention, source and target locations, and the transmitted information. In the event that more than 5% of transmitted information is unprintable, hex dumps are given.
–script-updatedb
It is just important to upgrade the database in the event that you have included or expelled NSE scripts from the default scripts catalog or in the event that you have changed the classifications of any script. This choice is utilized independently from anyone else without contentions:
#nmap -script-updatedb.
A simple script scan by using the default settings of Nmap scripts
#nmap –sC {Target_IP}
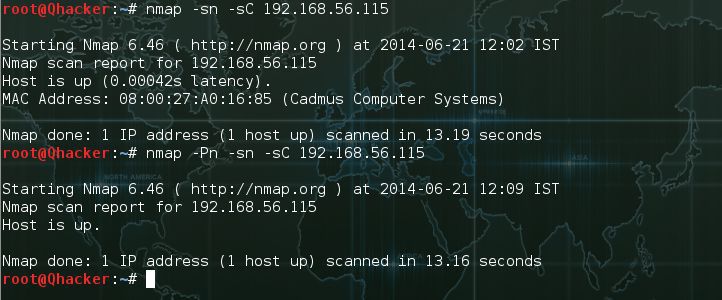
A script scan a target machine without port discovery. This scan only identify host is running or down.
#nmap -sn –sC {Target_IP}
#nmap –Pn -sn –sC {Target_IP}
This scan is used to scan networks without port scanning and host discovery.
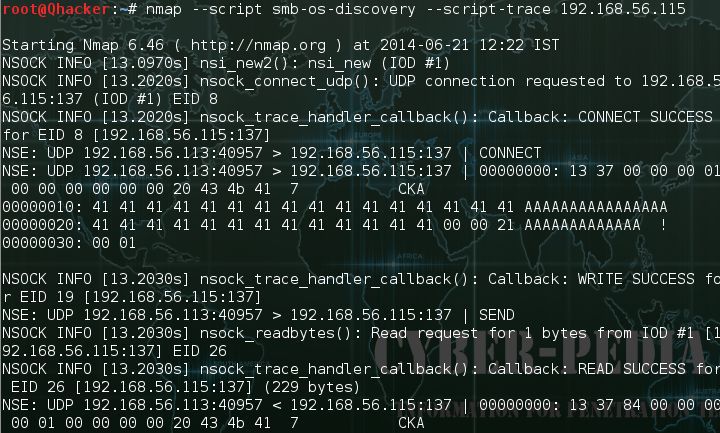
Pnetration tester can execute a specific script with script tracing.
#nmap –script smb-os-discovery –script-trace {target_IP_Address}
Run a particular script that takes a script argument





No comments:
Post a Comment